3.4.1. Device Security
3.4.1.1. Security Overview
The AM62x SoC offers a comprehensive set of security features that protect embedded Linux applications. This guide offers a starting point to understand and implement these capabilities as part of product development, with the following advantages:
Hardware-backed security - Leverages built-in security hardware for robust protection
Defense in-depth - Implements security at many levels including hardware, firmware, software to protect against wide range of attacks
Industry standards compliance - Incorporates security measures such as secure boot, TrustZone, and crypto acceleration that can help meet requirements in standards such as IEC 62443 and NIST guidelines
Flexible implementation - Allows security features that can be tailored to specific application needs
3.4.1.2. Security Domains
Below is an overview of the security framework’s main domains:
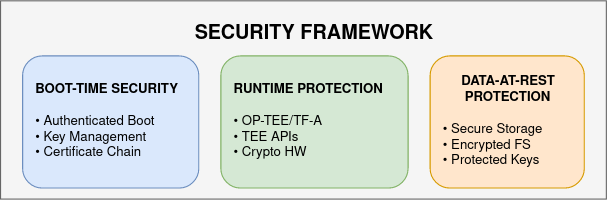
These security domains create a chain of trust protecting the AM62x SoC from boot through runtime and storage, ensuring system integrity and data confidentiality.
3.4.1.3. Security Features at a Glance
The following table lists some of the key Security Features:
Security Feature |
Description |
Links |
|---|---|---|
Authenticated Boot |
Verifies each boot component to ensure only authorized code executes on the device |
|
Crypto Acceleration |
Hardware driver support for cryptographic algorithms |
|
Secure Storage |
Protection mechanisms for sensitive data |
|
SELinux |
Kernel security module providing policy-based access control for processes, files, and system objects |
|
Trusted Execution |
Implementation of secure monitor (EL3) firmware that manages the secure boot process and TrustZone transitions |
|
Trusted Execution Environment that enables isolated execution of security-sensitive applications and services |